With the increase in tick activity and the expanding concerns about Lyme Desease in Canada, it would only make sense to have an application where mobile users can report ticks for image identification, and see local tick populations in thier local areas.
Welcome to the Canadian made eTick Mobile application by Bishop's University.
Over the last 6 months there has been quite a bit of media hype about eTick, and its rapidly growing crowed sourced submission of report ticks. It would seem however that this rapid growth has also lead to a problem with a core foundation of mobile based applications, API Security.
Prior to the publishing of this blog, The eTick team at Bishop's University was given 30 days notice of any issues found.
Timeline:
- On August 3rd an initial notice to eTick was sent
- Confirmation of the Privacy Policy and "protecting" user details was confirmed
- On August 16th confirmation of the fix prior to the 30 days notice was recieved from eTick
- On September 2nd, the solution indicated by Bishop's University has still not been implemented
- September 5th, The Users private information has been removed from the publicmetas API Endpoint
As a user of the eTick mobile app, I was reviewing one of my previous submissions and came across a few indicators of concern about the Web App portion of the platform that required further investigation. After about 20 minutes of investigation two major issues with the platform came to light.
eTick website and the exposure of private information.
The eTick website, contains a Privacy Policy which states:
In addition to public data, eTick.ca and the eTick mobile application also collects your username, name and e-mail address. That information, however, is only visible to eTick administrators and may be used to communicate with you and/or generate aggregate data about user numbers per province. No personal contact information is shared with a third party or made available to the public.
Last update: March 17, 2020
The basis for the Data Breach portion of this report is based on the violation of that statement, and the exposure of names, and emails of users submitting reports.
Improperly designed API - Exposing more information than needed.
As part of the Mobile Application and Web App feature set, there is the ability to see reported ticks in your general area. This feature depends on a "publicmetas" API to obtain data about user submissions. God bless developers and thier desire to make things flexible, and powerfull, however you need to ensure that you are not exposing "private" information about your users when you do so. This is exactly the case with the eTick public metas API endpoint
Using a common linux command line utility "curl", you can download several thousands or submissions which contain "private" user information.
curl "https://www.etick.ca/api/publicmetas?lang=&page=1&limit=2000
which results in the following results
{
"observation_id": 6111,
"number_of_individuals": "0",
"observationstatus_id": 2,
"hosttype": 3,
"created": "2020-05-24T14:49:11+00:00",
"checklist_id": 5678,
"validity_id": 1,
"photo": [{
"photo_id": 10892,
"observation_id": 6111,
"photo_path": "B4D105AE-A1C5-3E28-187B-EA3234446625.png",
"photo_name": "photo_name_ac.png",
"photographer": null,
"observationtype": 1,
"isdeleted": 0,
"created": "2020-05-24T14:49:11+00:00",
"updated": "2020-05-24T14:49:11+00:00"
}],
"Species": {
"latin_name": "Ixodes scapularis",
"english_name": "blacklegged tick"
},
"Site": {
"site_id": 6033,
"locality": "york region forest porritt tract",
"municipality": "whitchurch-stouffville",
"province_id": 5,
"latitude": "44.031810",
"longitude": "-79.347675",
"report_province_id": 5
},
"Province": {
"country": "Canada"
},
"Checklist": {
"dateidentified": "2020-05-19"
},
"Users": {
"username": "google_88A4A381-898C-A088-1880-62EB77B0714",
"first_name": "Bob",
"last_name": "W",
"user_id": 6212,
"email": "bobsfakeemail@gmail.com"
}
}, This record is the tick I submitted back in May 2020
The inclusion of that last "Users" object which contains user information, is in direct violation of the eTick Privacy Policy, and users expectation of the platform.
Improper form submission checks lead to modification of other users submissions.
Upon further investigation of the WebApp, is was discovered that while users can see all submissions, there is an "edit" link which appears when a user views thier own posts.
eg. [edit] - > https://www.etick.ca/etickapp/edit/report-index/6xxx".
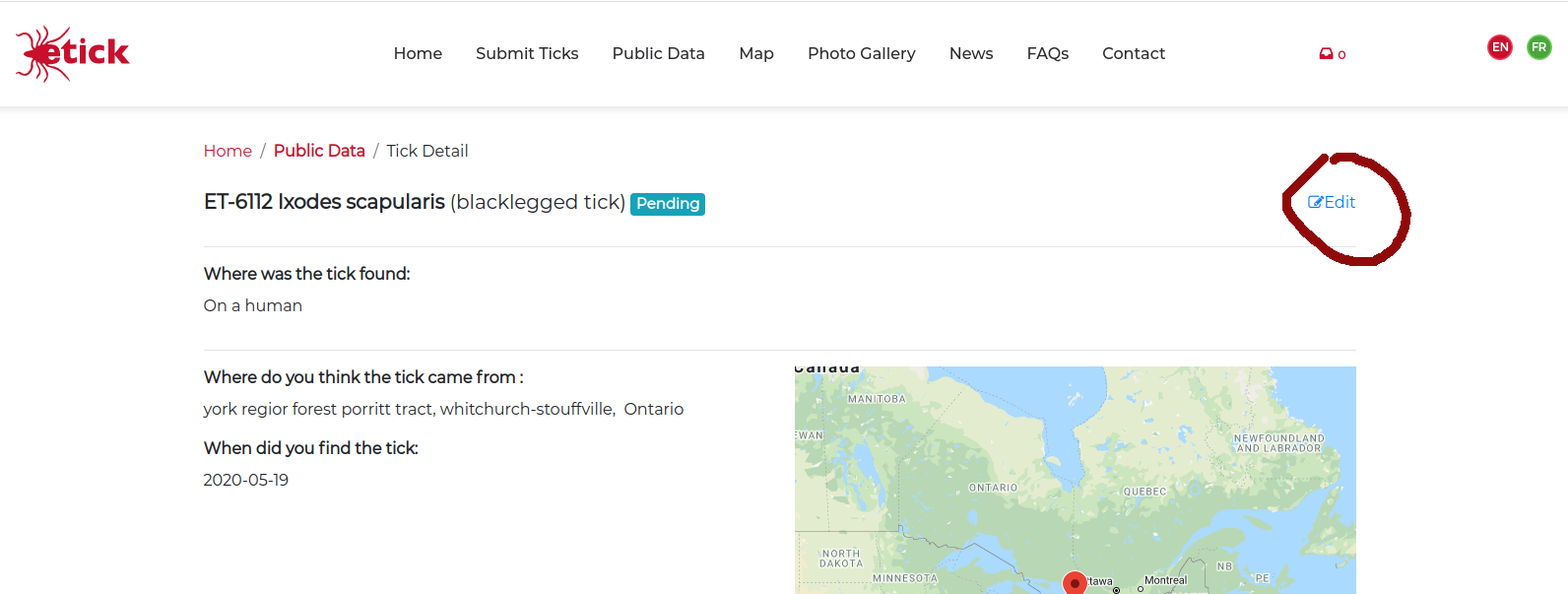
By using this URL and changing the report ID, you can identify any submitted report on the system and by combining the form submission with something like curl, you can modify the report id on the submit, and override/change other users submissions on the system. While an initial attempt at security was made to hide/show the edit link, there was no underlying userid to form ownership check, when changes are made and submitted. Again a basic mistep when trying to roll your own security in applicaitons. Most standard frameworks provide this level of security on aspects of an application including form submissions.
Summary:
- Don't roll your own applicaiton security, use a framework which provides it.
- Application / API extensibility is fine, but ensure you employ the proper security infrastructure for it
- Get a Security Audit done on on your applicaiton prior to launch